Introduction
DID Interaction
In this intricate communication network, DIDs act as unique identifiers that empower individuals to have complete and exclusive control over their own online identity. Through a set of technologies such as DID Documents, verifiable credentials, and Decentralized Web Nodes, DIDs interact to enable a secure and trustworthy exchange of personal information among various identities. In this section, we will delve into how DIDs communicate, resolve, and establish connections to provide an autonomous and safeguarded experience in the vast digital world.
Decentralized Web Node
A DWN functions as a mailbox or interaction point to receive and store messages in a decentralized environment. Its primary function is to enable communication and data exchange between different identities and agents. By resolving the associated DID Document of a DID, the location of an individual's DWN can be discovered, allowing for secure and reliable message delivery.
The operation of a DWN involves several aspects:
DID Resolution: A DWN has the capability to resolve DIDs (Decentralized Identifiers) and find the associated DID Document of a subject. By resolving a DID, the DWN obtains the necessary information to establish a connection with the owner of the DID and communicate with them.
Message Reception and Storage:The DWN acts as a mailbox or interaction point to receive and store messages sent by other actors in the ecosystem. Messages can include requests for credential creation, credential issuance, or credential verification.
Security and Authentication: The DWN ensures that received messages are authentic and have not been altered during transmission. This is achieved through cryptographic encryption and signing techniques that guarantee the integrity and authenticity of the messages.
Peer to peer Communication: Once the DWN resolves the associated DID Document of a DID, it can establish point-to-point communication with the owner of the DID. This enables direct and secure interaction between different identities and agents within the ecosystem.
In summary, a DWN serves as a reliable intermediary for communication and data exchange in decentralized systems, ensuring the privacy, security, and authenticity of interactions between different identities within the context of Self-Sovereign Identity.
WACI-DIDComm
WACI-DIDComm is a combination of two related technologies: the WACI protocol (Wallet and Credential Interaction) and DIDComm (Decentralized Identity Communication).
WACI is a protocol that defines how verifiable credentials are issued, presented, and verified in a decentralized environment. It facilitates the interaction between digital wallets and verifiable credentials, allowing users to securely present their credentials to demonstrate the authenticity of their data in different contexts. WACI establishes standards and specifications for digital wallets to interact with verifiable credentials and perform various operations such as requesting credential creation, presenting credentials, and verifying identity.
DIDComm is an encryption scheme used to establish secure and reliable communication channels between different identities and agents in a decentralized environment. DIDComm is based on DIDs (Decentralized Identifiers) and the associated public and private keys to ensure privacy, security, and authenticity in interactions between different parties. Before establishing communication, the involved parties exchange their public keys so that each can encrypt messages that can only be decrypted with the corresponding private key.
Therefore, WACI-DIDComm combines the WACI protocol with the DIDComm encryption scheme to enable secure and reliable interaction. It employs DIDComm to establish secure communication channels between parties and uses WACI to carry out operations related to verifiable credentials, such as presentation and identity verification.
DID Document Services
The "services" section in a DID Document is an important part that allows defining additional services associated with the DID. These services can encompass anything related to the subject of the DID and can be useful for their online interactions.
By including information about associated services, it simplifies interaction and communication between the DID subject and other parties.
In the DID Document, a service pointing to a DWN can be specified. However, this is achieved by including an endpoint URL (a link) in the "service" section that indicates where the DWN is located and how it can be accessed. In this manner, communication with the DWN is accomplished by resolving the DID Document and utilizing the service information provided within it.
{
"id": "did:example:alice",
"service": [{
"id":"#dwn",
"type": "DecentralizedWebNode",
"serviceEndpoint": {
"nodes": ["did:example:host", "https://dwn.example.com"]
}
}]
}
Verifiable Credential Issuance Flow
To ensure communication privacy and authenticity, it's crucial to have an appropriate transport layer for messages. To achieve this, we rely on the DWN service, which is a decentralized and interoperable solution. This service operates based on specific rules that enable responding to requests by sending messages to the DID that has configured the DWN as its service.
In the following example, we present a flow for obtaining verifiable credentials. On one hand, there's an individual or user with their wallet who wants to obtain a verifiable credential. On the other hand, there's a web portal responsible for issuing the credential.
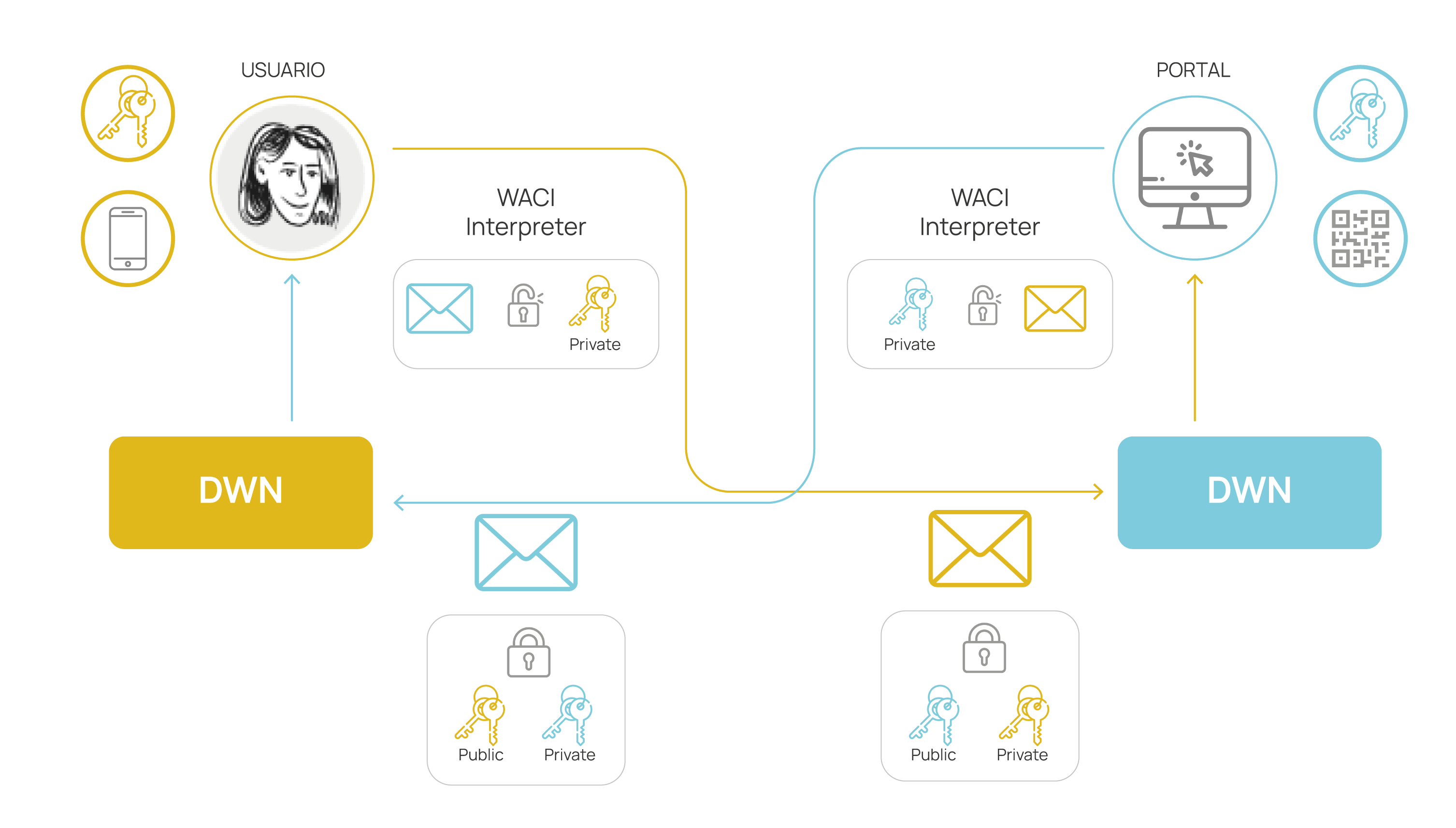
When a user wants to communicate with the portal, they first scan a QR code to obtain the portal's DID and initiate the communication. To achieve this, they resolve the DID Document to discover the DWN, which is configured as a service in the "services" section of the counterpart's DID Document.
The individual sends the message to the portal's DWN, and this service is responsible for reading and interpreting the received messages. For this purpose, it utilizes the WACI Interpreter, as not all messages from the DWN are of the WACI type. If the message is interpretable, the DWN passes it to the interpreter; otherwise, it may discard it.
The portal receives the WACI message and understands that a credential flow is initiated. It processes the message, sends it to the WACI interpreter, and responds accordingly. To respond, the portal reads the individual's DID Document, activates its DWN service, and sends the appropriate message for that stage of the WACI flow.
It is crucial that messages sent to the DWN are encrypted with DIDComm to prevent malicious third parties from intercepting communication with the other party. DIDComm has the ability to encrypt and authenticate the message, ensuring the authenticity of the remote DID and its corresponding private key.
Through this layered and service-oriented system, we ensure secure and reliable communication in the handling of sensitive and verifiable data.